Something went wrong. Please refresh the page and try again.
Something went wrong. Please refresh the page and try again.
Notifications can be turned off anytime from settings.
Item(s) Added To cart
Qty.
Something went wrong. Please refresh the page and try again.
Something went wrong. Please refresh the page and try again.
Exchange offer not applicable. New product price is lower than exchange product price
Please check the updated No Cost EMI details on the payment page
Exchange offer is not applicable with this product
Exchange Offer cannot be clubbed with Bajaj Finserv for this product
Product price & seller has been updated as per Bajaj Finserv EMI option
Please apply exchange offer again
Your item has been added to Shortlist.
View AllYour Item has been added to Shopping List
View AllSorry! ISO 27001 (e-Certificate Course)-Online Video Training Material, Technical support, Verifiable certificate. is sold out.



You will be notified when this product will be in stock
Syste
m (Hardware/Software)
Requirements
| Operating
Software | Windows XP or
Higher
| Processor | Minim
um P4 or Higher
| RAM | 1 GB or
Higher
| Browser | Any
| Recommended Internet
Speed | Minimum 1MBPS
| Supported Browser
Plug-ins | * Updated
Flash Player, * Update Java
| Other
Requirements | Speaker or
headphone | | |
Course Curriculum
Section1:Introduction of ISO 27001 Lecture1:Introduction
Section2:Information Security Lecture4:Defining Information Security
Section3:Information Security Management System Lecture8:Information Security Management System Introduction
Section4:Risk Assessment Lecture13:Risk Assessment Part 1
Section5:Quantative Risk Assessment Lecture22:Quantative Risk Assessment Part 1
Section6:Risk Communication Lecture25:Risk Communication Part 1
Section7:Risk Policy, Roles, Responsibilities Lecture27:Risk Policy, Roles, Responsibilities Part 1
Section8:Qualatative Risk Assement Lecture30:Qualatative Risk Assement Intro
Section9:Risk Assessment Methodology Lecture36:Risk Management Standards Step 1 & 2 Part 1
Section10:Risk Mitigation and Risk Mitigation Strategies Lecture43:Risk Mitigation and Strategy Part 1
Section11:Risk Management Tools & ISO STandard Clauses Lecture48:Risk Management Tools & ISO Standard clauses part 1
Section12:ISO 27002 Introduction & Scope Lecture55:ISO 27002 Introduction & Scope Part 1
Section &
Section 5 Security Policy Part 1 Lecture58:ISO 27002
Section &
Section 5 Security Policy Part 2 Lecture59:ISO 27002
Section &
Section 5 Security Policy Part 3 Lecture60:ISO 27002
Section 6 Organization of Information Security Part 1 Lecture61:ISO 27002
Section 6 Organization of Information Security Part 2
Section13:Asset Management Lecture62:
Section 8 Human Resources Security Part 1 Lecture63:
Section 8 Human Resources Security Part 2 Lecture64:
Section 9 Physical and Environmental Security Part 1 Lecture65:
Section 9 Physical and Environmental Security Part 2 Lecture66:
Section 10 Communication and operations management Part 1 Lecture67:
Section 10 Communication and operations management Part 2 Lecture68:
Section 10 Communication and operations management Part 3 Lecture69:
Section 10 Communication and operations management Part 4
Section14:Access Control Lecture70:
Section 11 Access Control Part 1 Lecture71:
Section 11 Access Control Part 2 Lecture72:
Section 11 Access Control Part 3 Lecture73:
Section 11 Access Control Part 4 Lecture74:
Section 12 Information systems acquisition, development and maintenance PArt 1 Lecture75:
Section 12 Information systems acquisition, development and maintenance PArt 2 Lecture76:
Section 12 Information systems acquisition, development and maintenance PArt 3 Lecture77:
Section 12 Information systems acquisition, development and maintenance PArt 4
Section15:Information Security Incident Management Lecture78:Information Security Incident Management Part 1
Section 14 Business Continuity Management Part 1 Lecture81:
Section 14 Business Continuity Management Part 2 Lecture82:
Section 15 Compliance Part 1 Lecture83:ISO 27002
Section 15 Compliance Part 2 part 1 Lecture84:ISO 27002
Section 15 Compliance Part 2 part 2
Section16:Certification ISO 27000 in Organization Lecture85:Certification ISO 27000 in Organization Part 1
Section17:Hazard & Strategic Risk Lecture90:Hazard & Strategic Risk Part 1
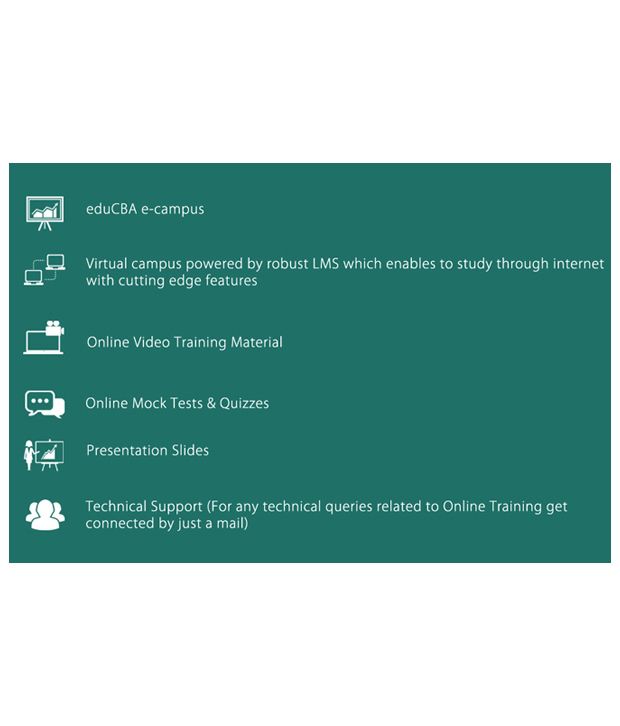
Benefits
USP of the product
How to use? (Steps to use Study Material)
To get more information, you may want to watch the video below
The images represent actual product though color of the image and product may slightly differ.
Register now to get updates on promotions and
coupons. Or Download App